Healthcare Claims
Analysis Objectives and Sample Chart
ACG fraud detection models employ a powerful combination of data mining, predictive modeling, statistics to detect potential fraud and abuse. Our models are not dependent upon data from previously detected fraud cases. Our approach uses various data interrogation techniques such as query and reporting, data association, clustering, etc., to identify anomalies and suspicious activities from the data itself.
The models enable the user to adapt to the changing patterns of fraudulent claims submissions as they evolve in real time. The models are not dependent upon knowing the attributes of the last fraudulent claim to be effective. The models are built to detect suspicious patterns in the claim data itself, their association with other claims data, and providers are compared against their peers. The anomalies and suspicious patterns are presented to an investigator with their reasons for final determination of fraudulent activity.
The standard approach, limiting in our opinion, takes known cases of claims fraud and uses the characteristics of these claims to train a model to spot these characteristics in the future. In other words, the approach’s effectiveness depends on learning from past known incidences of fraud. If past fraudulent claims go undetected or characteristics change, the model will miss them every time.
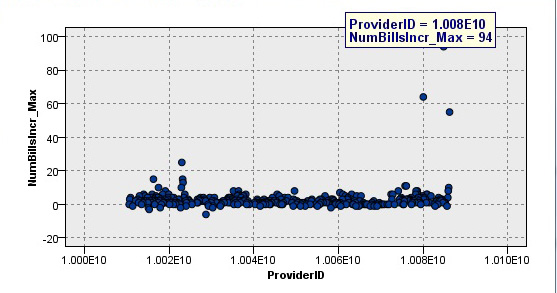
Our approach uses the current data set to identify possible fraudulent claims. For example, the following graph illustrates a report generated from a healthcare fraudulent claims project. The chart shows three providers (outliers) with the greatest increase in the total number of bills over a month’s time (suspected of claim acceleration practices):
Data Analyzed, Models Used and End Results Achieved
Historical healthcare claims data are tested to identify behavioral characteristics and patterns associated with claim fraud. Some of these tests are specifically designed to capture known elements of suspicious behavior. Other tests are designed to compare the claim with its like counterpart. Models are then built based on these tests and their associated variables and used in recognizing possible fraud in future claim submissions. Examples of these suspicious activities include the following:
• Generating numerous claims for a large number of patients over a period of time.
• Generating multiple copies of claims for the same person and procedure submitted all at the same time or over a period of time.
• Originating a claim covering a number of procedures where only one was required.
• Originating numerous claims for the same patient from multiple providers.
• Originating claims for many more doctor visits than actually required for the diagnosis.
Benefits Realized and Reference Case Study
• Significant reduction in losses from paying fraudulent claims.
• Catch claim fraud before the payment is made; avoiding the need to recover the money.
• Reduce problem claims by encouraging submitters to validate and verify claims before submitting them.
• Identify issues with medical policies, contracts, processing procedures, etc., from model’s output.
• Identify errors in billing, payment or coding systems from unusual claim patterns.
Click on the link entitled Improving Healthcare Claim Fraud Detection found in the Resource Center for the case write-up.